What's the deal? I'm testing using https://coveryourtracks.eff.org Is it truly unique (and repeatable), or is it perhaps being randomized on every request?
I've tried normal Firefox, Mull, and IronFox. With and without jShelter.
I'm using my phone. Stock Android on a Pixel 7 Pro.
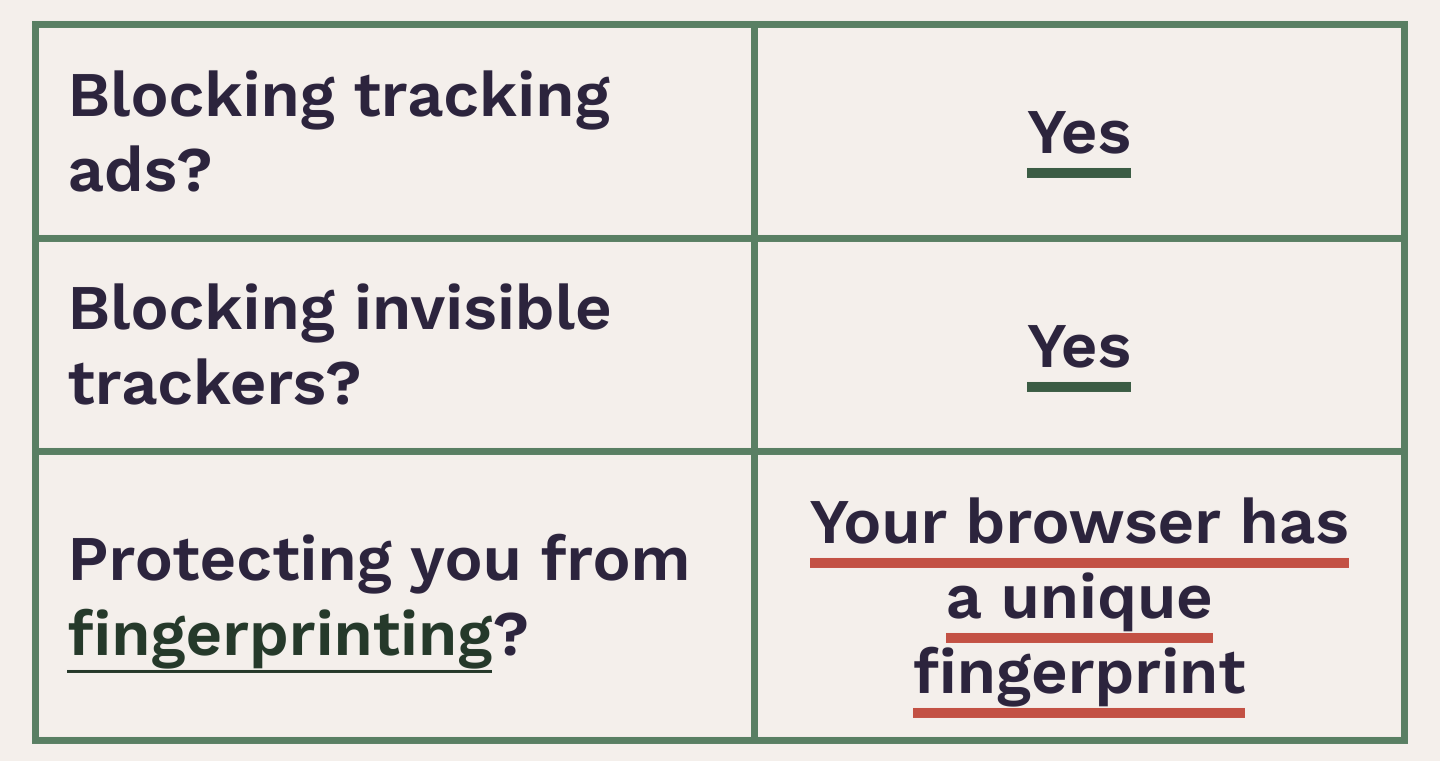
In DDG Browser I have a "nearly unique" fingerprint.
I installed CanvasBlocker and disabled privacy.resistFingerprinting in IronFox (since CanvasBlocker said to), and my fingerprint is still unique. I guess I'm not surprised since I think CanvasBlocker is designed to randomize canvas fingerprinting.
Any tips on having even a shred of privacy when browsing the web on Android?
#Update
The biggest identifying characteristics are screen size and user agent. User agent can be faked with an extension. I can't exactly change my screen size.
I don't know what exactly what I did, but I managed to improve to "nearly unique" in IronFox. I think all I did was install Cookie Autodelete. It's an extension I've used for a long time in Mull, and finally got around to installing it. Then I installed "User-agent Switcher" and chose a Chrome user-agent and now I'm back to "Unique". 🤔
EFF mentioned Tor Browser having some other best anti-fingerprinting, so I tried installing that. "Unique Fingerprint". Again, maybe that's fine if it means it's randomized on every request. Does anyone know if that's the case? If part of the fingerprint is a hash of canvas data and WebGL data, etc. Then I can easily see your fingerprint being unique if a browser or an extension is intentionally fuzzing that data.
#Update 2
I tried Fennec with just jShelter, uBlock Origin, and Cookie AutoDelete (not that I think those last two matter).
Obtained a "randomized fingerprint" result. Success?
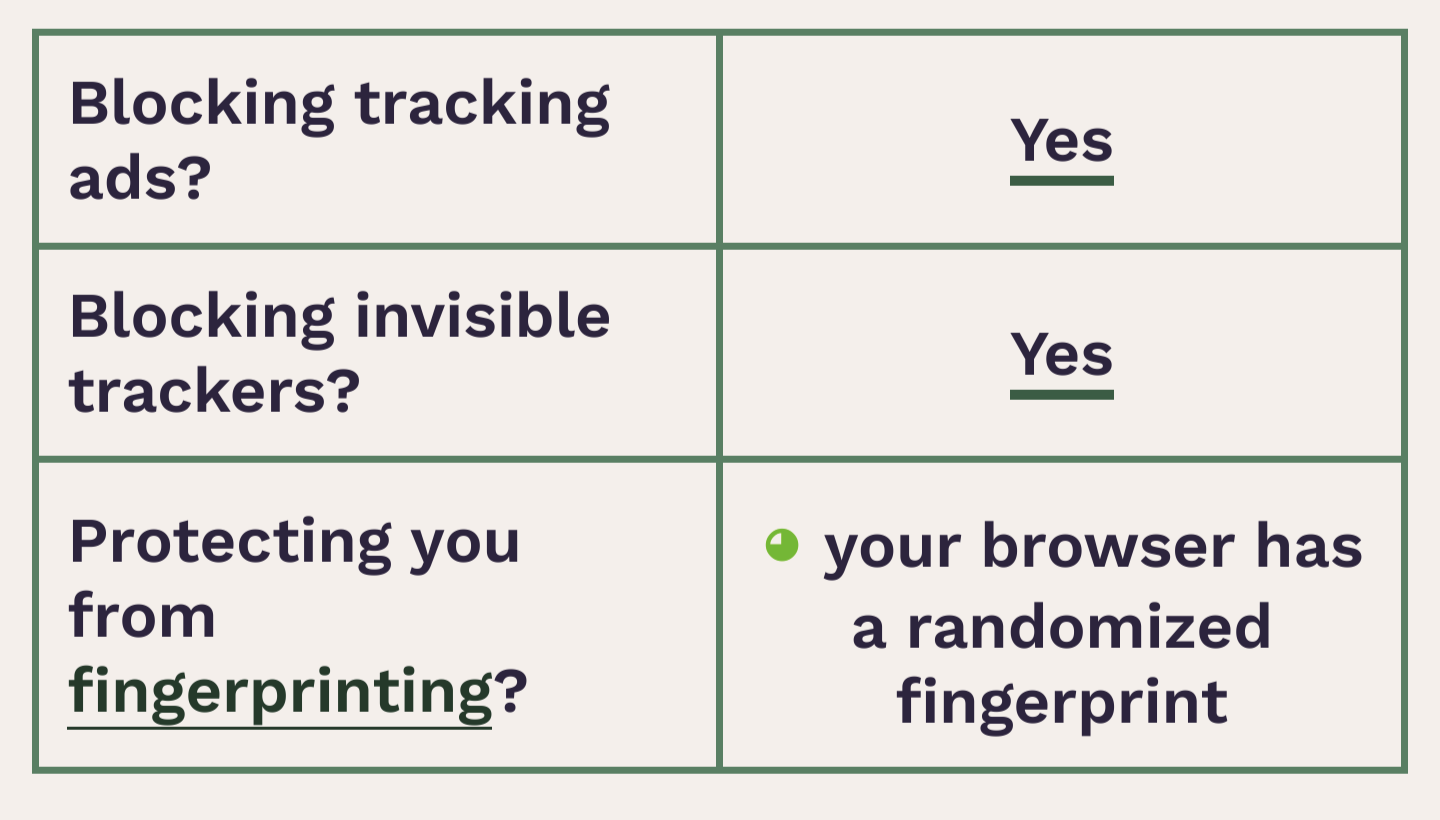

I don't understand the question. What is "noise"?
The reason it's so hard is because your browser is telegraphing all sorts of information about your computer to the sites you visit. Some of those things are varying degrees of necessary in order for your browser to function. For example, your time zone is needed in order to show you the correct time for events. There are a hundred of these identifiers. And many nerds like you and me are going to have weird display sizes or use weird browsers or disable certain functions, etc.
If you go to deviceinfo.me, it's basically a mirror that reflects back at you all the information your browser is feeding it.
Funny enough, not sending info at all can also be used to fingerprint you. That's why the main strategy for anti-fingerprinting in browsers like TOR is to just send all of the most common info in order to blend in.
Also companies started using "Do Not Track" requests to actually track you.
Im saying to mix in random data into all the information u send. If everyone has a slightly weird display size nobody does etc etc.
Yep, I agree. Not seen any tools that can do that though. I believe Safari has some randomization built in. But fuck Apple.